Project Description
What is a revision-compliant archiving solution?
Since the inception of the General Data Protection Regulation (GDPR), organisations must keep hold of data “for no longer than is necessary for the purposes for which it is being processed”. When other compliance needs (MiFID II, etc.) that have to be met, it’s getting complicated. The new right to erasure (also called the “right to be forgotten”) is not absolute – some organisations may have a legal requirement or other legitimate grounds to continue processing a person’s data even if that person requests otherwise.
CLIENT PROFILE
Our client is one of the largest global retailers with thousands of stores worldwide and highly skilled IT departments and teams across the board.
| Industry | Retail |
| Employees | 100.000+ |
| Year founded | 1984 |
| Publicly listed | No |
CHALLENGE
The client required a solution to archive large quantities of documents, such as building permits, rental agreements, employer and supplier contracts, and shopping receipts. The legal requirements for retention periods were specifically challenging.
PROCESS
In order to archive data in a compliant manner, however, several pre-requisites from both an infrastructure and process perspective had to be met with respect to data protection and privacy laws. The project was organized in three distinct steps:
1. DISCOVERYOnce all milestones, deliverables, timeline and the budget were agreed upon, we kicked-off the implementation of the Proof-of-Concept:
|
|---|
2. WORKSHOPWe conducted several senior- and middle-management workshops and covered the following aspects:
Findings from both the workshops and system audits were modulated in the feasibility report. |
|---|
3. FEASIBILITYWe conducted a detailed feasibility report prior to taking stock on all relevant software requirement specifications:
|
|---|
SOLUTION
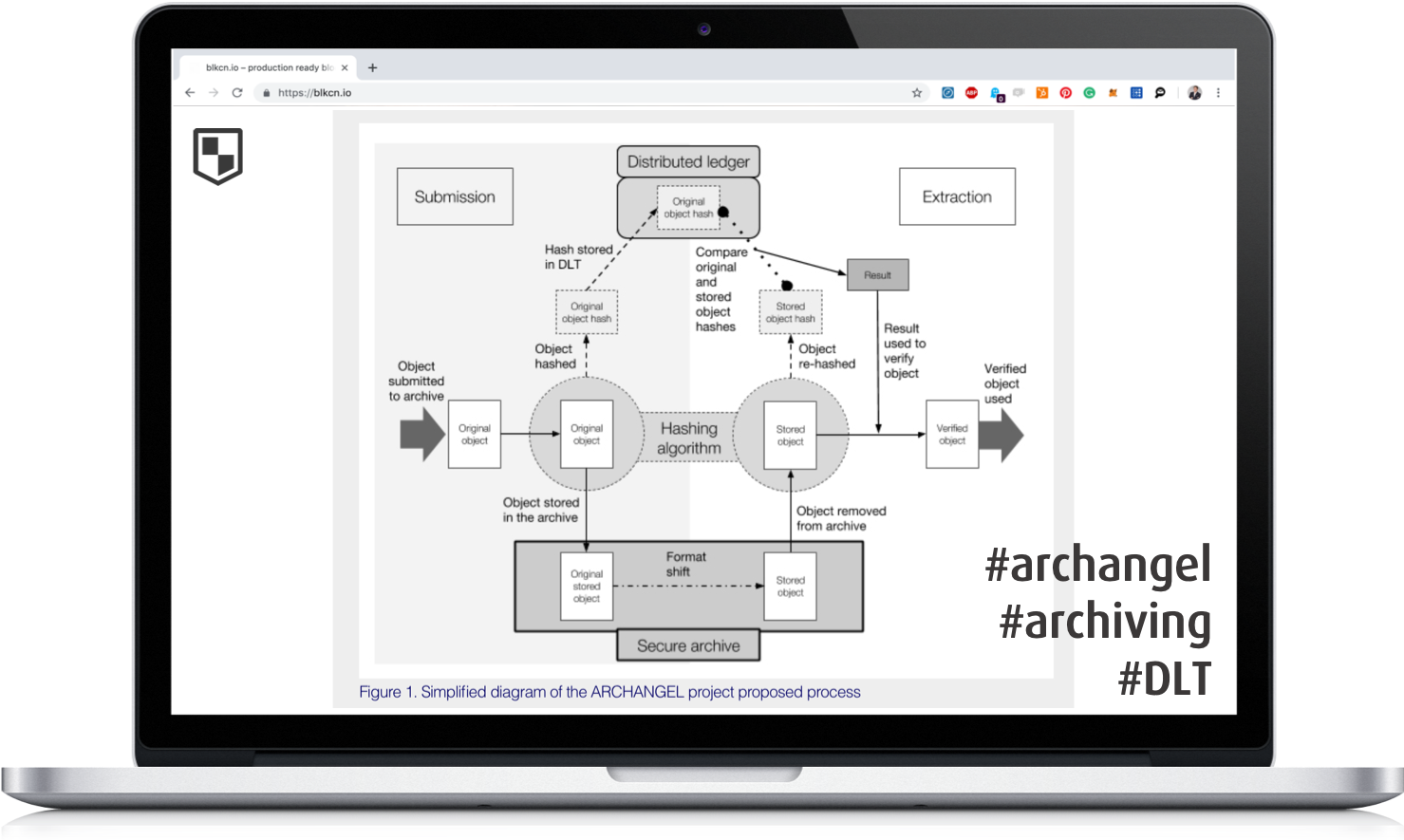
We designed a configuration in Hyperledger Fabric to track every storage-related user action in connection with a hash of the document to guarantee the authenticity of stored documents.
RESULTS
The client received a detailed business impact analysis with an overview of the target model, system architecture design, proposed staging environment, modulated process landscape and required testing & security audits.
DETAILS
Click on the toggles to find out more about the specific project details:
As one of the biggest global retailers with thousands of stores worldwide, our client's IT management provides the most innovative, best-in-class IT solution to the entire organisation.
Each store globally is required to archive large quantities of various documents, such as building permits, rental agreements, employer and supplier contracts. However, shopping receipts for purchases made in a store represent the largest data storage challenge. Besides the number of receipts, the legal requirements for retention periods are specifically challenging.
As all documents are stored in isolated, expensive WORM storage solutions today, the existing solution was replaced by a document management solution that does not rely on WORM storage, but nevertheless fulfils the regulatory requirements of revision- and audit-compliant archiving. Metadata is separated from the storage layer and stored in a Mongo DB cluster, hence allowing performant searches and browsing the file base in client applications. The files are stored encrypted and can only be accessed by whitelisted applications. Moreover, the company lacks control over what type of data is shared, whom it is shared with, when, and for what purpose. Often large sums are invested to utilize this data and run comprehensive analytics.
An audit-log is written on a distributed ledger tracking every action/event/request in order to comply with the existing revision safeguard codes.
In summary, the company's goal was to develop a DLT-based archiving solution with the objective to provide the following functionality for both its thousands of stores and subsidiaries and partner companies:
- Secure and scalable DLT-based archiving solution
- Multiple encryption layers
- Secure data transfer and sharing
- Client management
- Partner management
Management actors
The management actors are involved in user creation, archiving use & management and processes management. For our purpose, we defined the following management roles: super admin, document administrator, storage administrator, process administrator, and security administrator.
Non-management actors
Besides systems-side users, we differentiate several non-management users: partner user – users that did perform the KYC process, but cannot store and archive any assets on the platform, affiliate users – users that performed the KYC process, are classified as direct affiliates of our client and are allowed to store and archive documents and corporate users – a platform user directly associated with the retailer that is validated as a user and can perform several read and write transactions within the platform.
The following core functionality was provided in scope with the PoC:
- Secure and scalable private, permissioned distributed ledger solution
- Document class based definition of retention times
- User accounts lifecycle management: account registration, account login/logout, ban and recovery
- Store file operations management
- Storage read request operations management
- Document lifecycle management: business logic imposition for each type of document, transfer of documents between users' accounts on the platform
- Web interfaces
- Mobile interfaces
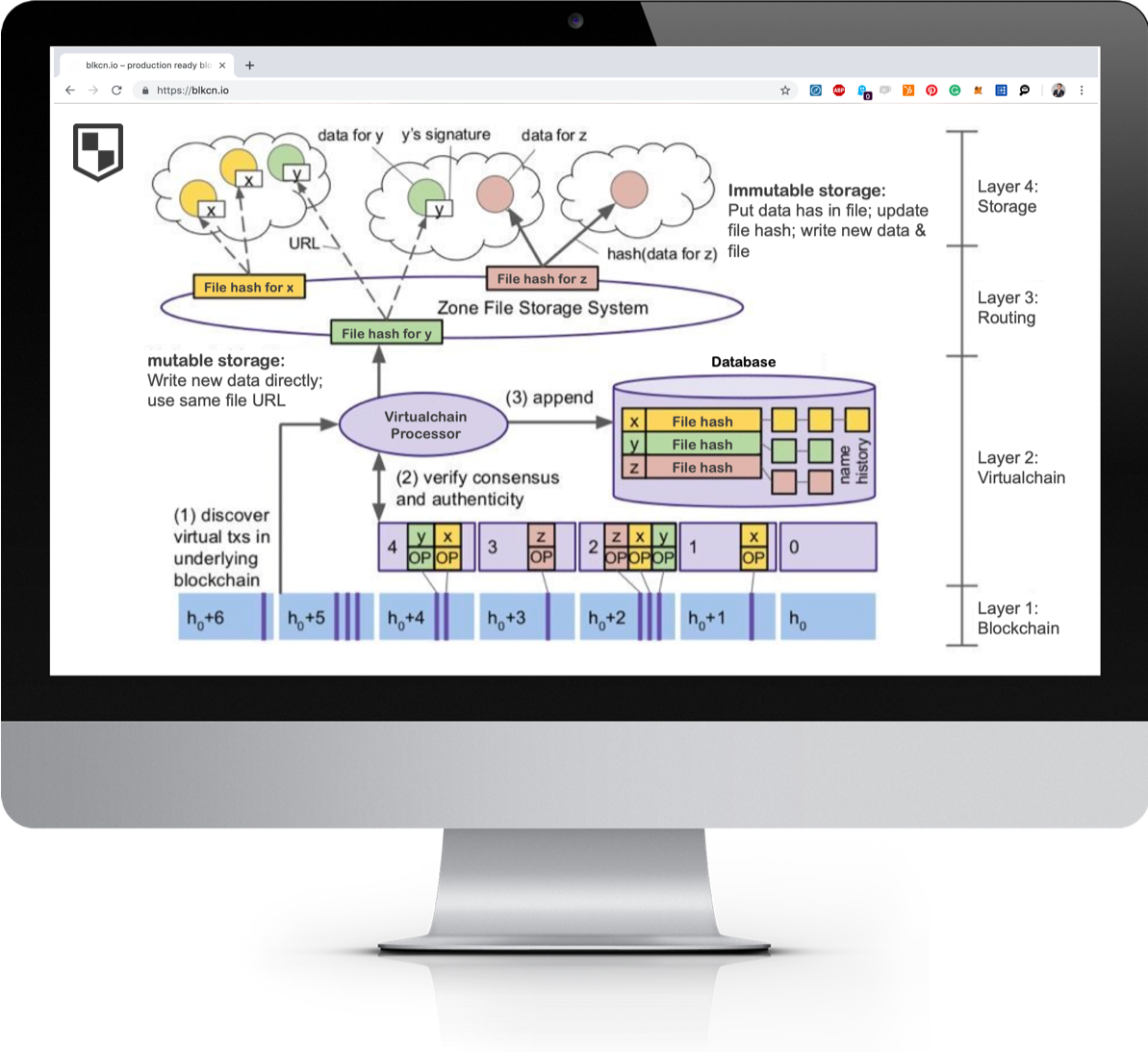
The main components are the 4 layers: blockchain, virtualchain, routing and storage.
The architecture was designed similarly to the figure depicted below:
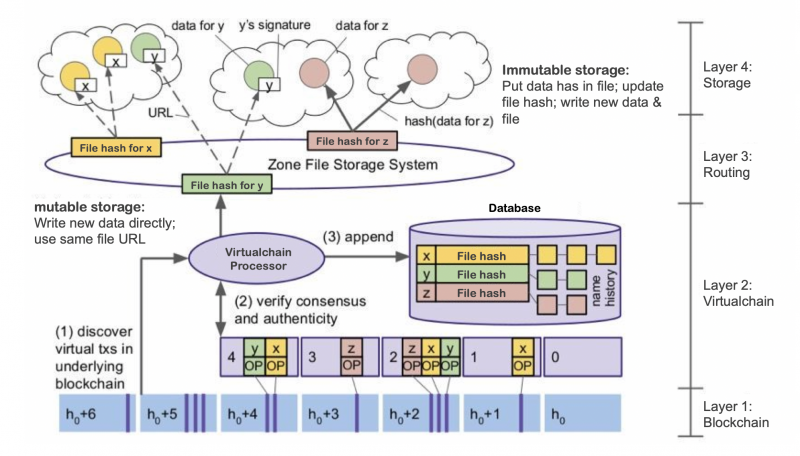
The virtualchain approach allows the client to ensure interoperability of solutions; if at any point the underlying technology framework shall be changed, replacing is enabled by simply exchanging the file hashs written onto the virtualchain.
The project was completed within 20 weeks in an interdisciplinary team from both the client and us:
- Enterprise Architect «client»
- Lead Developer Backend «client»
- Lead Developer Frontend «client»
- Head of Digitalisation «client»
- Senior Project Manager «client»
- Chief Technology Officer «howtogetthemoney.com»
- Enterprise Architect «howtogetthemoney.com»
- Lead Developer Corda «howtogetthemoney.com»
- Development Operations Manager «howtogetthemoney.com»
- Project Management Office «howtogetthemoney.com»